7 Best Practices to Secure Your Mobile App (2024)

Mobile app security has become more crucial than ever. As businesses increasingly rely on mobile applications to drive operations, engage customers, and manage data, the need to safeguard these apps against evolving threats cannot be overstated. With the rise of sophisticated cyber-attacks and the increasing value of user data, implementing robust security measures is not just a recommendation; it's a necessity.
This article dives into the 7 best practices that are essential for securing your mobile application. These strategies are designed to help business owners, like you, protect your digital assets, customer data, and maintain a trustworthy reputation in the marketplace. From implementing advanced authentication measures to educating users about security, we will cover comprehensive methods to enhance your app's security posture in 2024.
1. Implement Robust Authentication and Authorization Measures

Strong Authentication: In the era of mobile apps, authentication goes beyond just usernames and passwords. Implementing strong authentication mechanisms is fundamental for safeguarding user accounts. This includes biometric authentication methods like fingerprint scanning and facial recognition, which are not only more secure but also provide a seamless user experience. Additionally, two-factor authentication (2FA) or multi-factor authentication (MFA) like Authy should be considered a standard practice. By requiring a second form of verification, such as a text message or an authentication app, the security of user accounts is significantly enhanced.
Authorization Controls: Authorization is equally important. This involves managing user access levels within your app. Not every user should have access to all features and data. For instance, administrative functions should be restricted to authorized personnel only. Implementing role-based access control (RBAC) ensures that users can access only the data and functions relevant to their role, thereby minimizing the risk of unauthorized access to sensitive information.
2. Ensure Secure Data Storage and Transmission

Data Encryption: Protecting data both at rest (stored data) and in transit (data being transferred) is critical. Data encryption serves as the first line of defense against data breaches. Using advanced encryption standards like AES-256 for stored data ensures that even if data is accessed by unauthorized individuals, it remains unreadable and secure.
Secure Protocols: When it comes to data transmission, it's vital to use secure and updated protocols. HTTPS, SSL/TLS protocols should be the norm for all data exchanges. These protocols encrypt data during transmission, preventing interception and ensuring data integrity and confidentiality.
3. Regularly Update and Patch Mobile Apps

In the world of mobile technology and cybersecurity, regular updates and patches are vital for maintaining app security. Cyber threats evolve rapidly, and staying ahead requires constant vigilance and timely action.
Frequent Updates: Regular updates are not just about adding new features or improving user experience; they are crucial for closing security gaps. Developers must stay informed about the latest security threats and vulnerabilities, ensuring that the app is fortified against them. This proactive approach in updating apps can significantly reduce the risk of security breaches.
Quick Patching of Vulnerabilities: When vulnerabilities are identified, quick action is essential. Delays in deploying patches can leave apps exposed to attacks. A system should be in place for the swift development and deployment of patches. This responsiveness not only protects the app but also demonstrates a commitment to security to the users.
4. Integrate Security at the Development Stage

Integrating security at the development stage is crucial for building a secure mobile app. This approach, often referred to as 'security by design', ensures that security is not an afterthought but a fundamental component of the app development process.
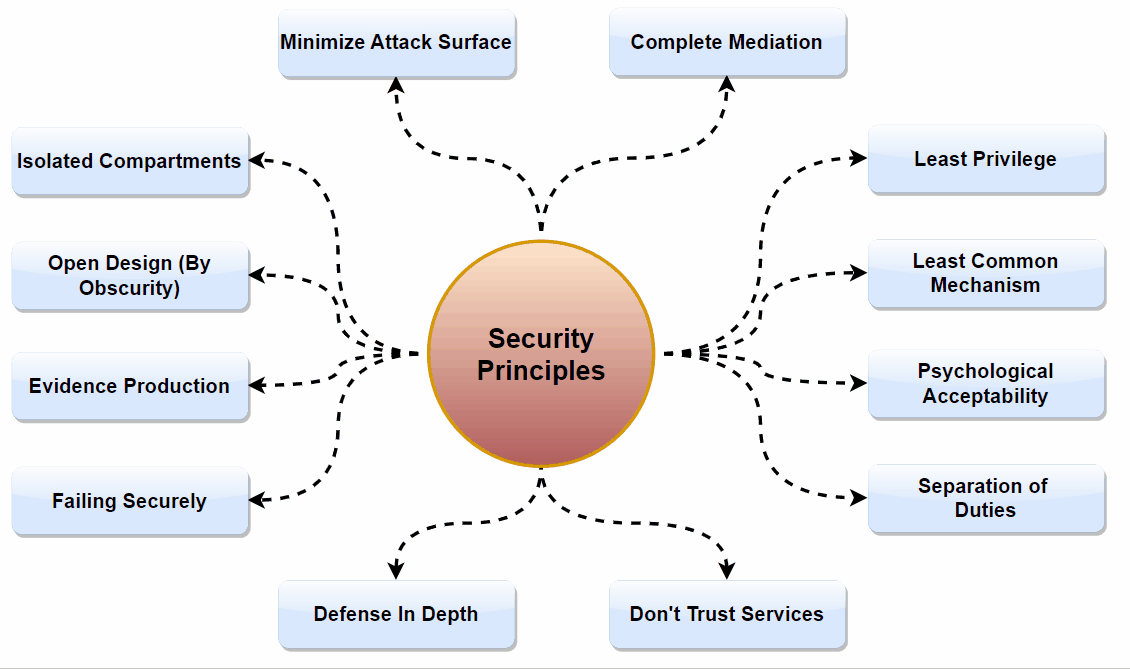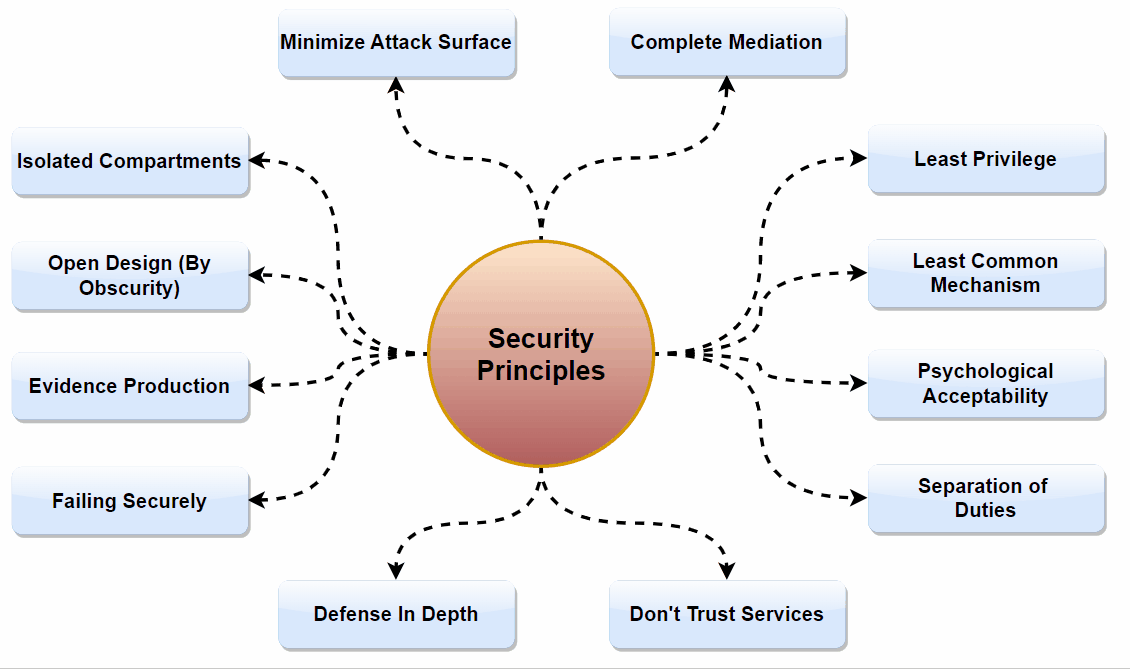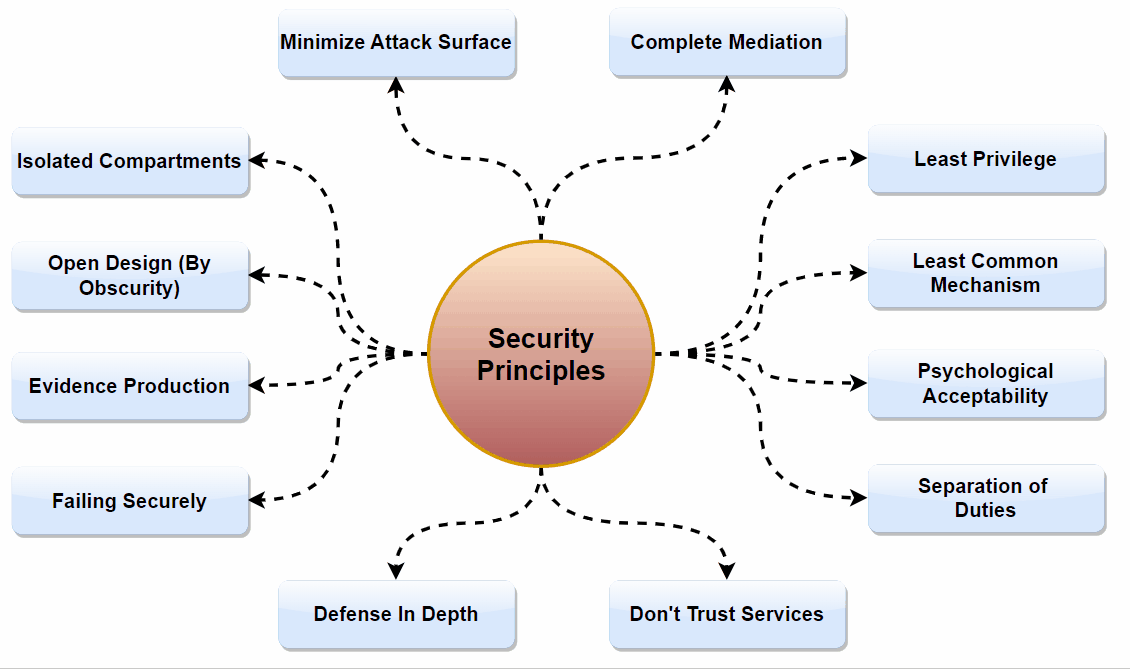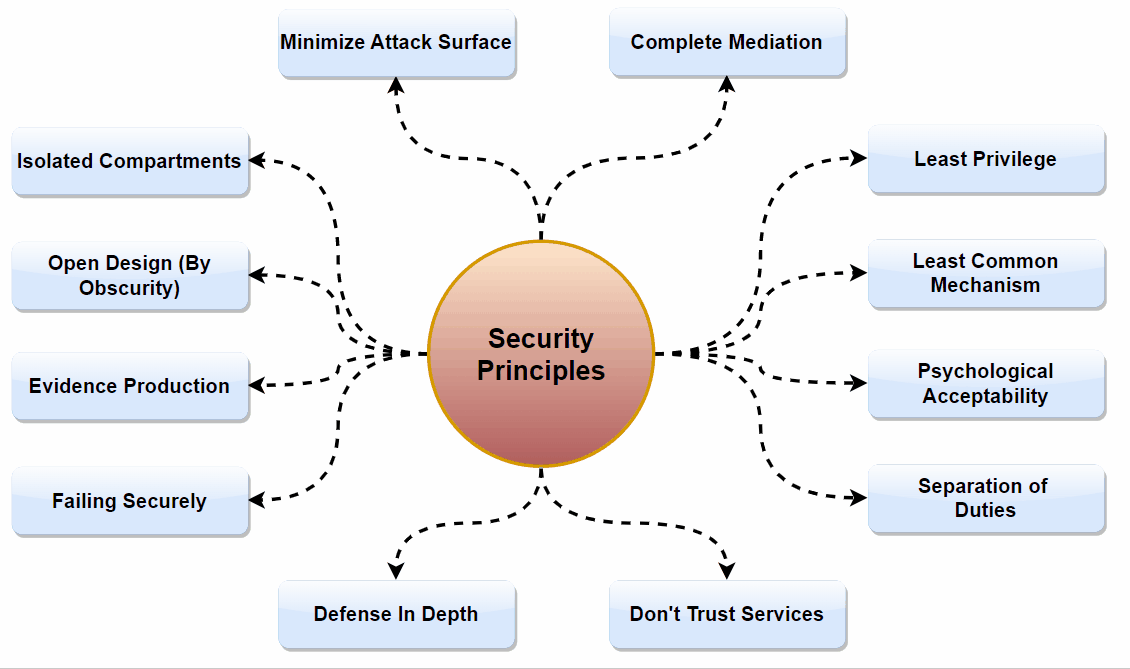
Security by Design: By incorporating security measures from the outset, potential vulnerabilities can be identified and addressed early in the development process. This approach is far more effective and cost-efficient than trying to patch security holes after the app has been developed.
Secure Coding Practices: Utilizing secure coding practices is fundamental. This includes adhering to coding standards that prioritize security, using code analysis tools to detect vulnerabilities, and educating developers about secure coding techniques. Implementing these practices significantly reduces the risk of security flaws in the app.
5. Conduct Thorough Security Testing and Audits

To ensure the robustness of your mobile app's security, conducting comprehensive security testing and regular audits is indispensable. These practices are crucial for identifying and addressing vulnerabilities before they can be exploited.
Security Testing: Various types of security testing methods should be employed. Penetration testing, where ethical hackers attempt to breach your app's defenses, can provide real-world insights into your app's security posture. Vulnerability assessments should be conducted regularly to scan for potential security weaknesses. These tests should cover all aspects of the app, including the code, APIs, and server environment.
Regular Security Audits: In addition to ongoing testing, regular security audits are essential. These audits should be conducted by independent security experts who can provide an unbiased assessment of your app's security. The audit can reveal areas where security practices may be lacking or outdated, providing an opportunity for timely improvements.
6. Utilize Application Shielding Techniques
Application shielding is a set of advanced techniques used to protect mobile apps from various attacks, including reverse engineering and tampering.
Code Obfuscation: This involves making your app's code more difficult to understand and reverse engineer. By obfuscating the code, you make it challenging for attackers to analyze the app and find vulnerabilities to exploit.
Runtime Protection: Runtime application self-protection (RASP) mechanisms can detect and prevent attempts to tamper with or modify the app during execution. This includes detecting jailbroken or rooted devices, which may be more vulnerable to security threats, and taking appropriate actions such as blocking access or alerting administrators.
7. Educate Users about Security Practices

The final, but no less critical, aspect of securing your mobile app involves educating your users about good security practices. User behavior can significantly impact app security.
Creating Awareness: Informing users about the importance of security and how they can contribute is vital. This can include guidance on creating strong passwords, recognizing phishing attempts, and understanding the importance of regular updates.
User-Friendly Security Features: Incorporate user-friendly security features that encourage users to adopt safe practices. For example, easy-to-use two-factor authentication, clear privacy settings, and regular security reminders can go a long way in enhancing overall app security.
Final Thoughts
In the digital age, where mobile apps are integral to business operations and user engagement, securing these applications is not just a technical necessity but a business imperative. The 7 best practices outlined in this article provide a comprehensive approach to mobile app security, ensuring that your application remains resilient in the face of evolving cyber threats.
By implementing robust authentication and authorization measures, ensuring secure data storage and transmission, regularly updating and patching your app, integrating security at the development stage, conducting thorough security testing and audits, utilizing application shielding techniques, and educating your users about security practices, you set a high standard for app security in 2024.
Remember, mobile app security is an ongoing process, not a one-time effort. It requires continuous attention and adaptation to new threats and technologies. As a business owner, investing in mobile app security is investing in your business's future, reputation, and the trust of your users.
As we move forward in 2024 and beyond, the importance of mobile app security will only continue to grow. By embracing these best practices, you can ensure that your mobile app is not only functional and user-friendly but also secure and trustworthy.
Key Takeaways
| Best Practice | Main Objective or Benefit |
|---|---|
| 1) Robust Authentication and Authorization | Enhances user identity verification and controls access to sensitive data. |
| 2) Secure Data Storage and Transmission | Protects data integrity and confidentiality both in transit and at rest. |
| 3) Regular Updates and Patching | Keeps the app secure against the latest threats and vulnerabilities. |
| 4) Security Integration at Development Stage | Ensures security is a core component of the app from the outset. |
| 5) Comprehensive Security Testing and Audits | Identifies and addresses potential vulnerabilities before exploitation. |
| 6) Application Shielding Techniques | Protects against reverse engineering and tampering. |
| 7) Educating Users on Security Practices | Empowers users to contribute to the app's overall security. |
Top Mobile App Security Companies
- Snyk: Snyk is a cybersecurity and developer-focused company that specializes in helping organizations find and fix vulnerabilities in their software applications and containerized infrastructure. Snyk's primary focus is on addressing security issues related to open-source code and dependencies, which are commonly used by developers when building software.
- Astra Security: Astra offers a comprehensive mobile app security platform that combines static, dynamic, and interactive application security testing (SAST, DAST, IAST) with real-time threat detection and protection. They are known for their user-friendly interface, scalability, and focus on continuous security throughout the development lifecycle.
- NowSecure: NowSecure provides a cloud-based platform for automated mobile app security testing, including static analysis, dynamic analysis, and penetration testing. They are known for their expertise in mobile security, their focus on developer productivity, and their wide range of integrations with popular development tools.
- Synopsys: Synopsys offers a comprehensive portfolio of application security solutions, including their Mobile Security platform. This platform provides static, dynamic, and interactive analysis, as well as threat modeling and code scanning capabilities. Synopsys is known for its deep security expertise, its broad range of solutions, and its commitment to innovation.
- HCL AppScan: HCL AppScan provides a suite of application security testing tools, including their Mobile App Security solution. This solution offers static analysis, dynamic analysis, and penetration testing capabilities specifically designed for mobile apps. HCL AppScan is known for its affordability, its ease of use, and its wide range of integrations.
- Checkmarx: Checkmarx offers a cloud-based platform for application security testing, including their CxSAST Mobile solution. This solution provides static analysis for mobile apps, helping to identify and fix vulnerabilities early in the development lifecycle. Checkmarx is known for its advanced static analysis capabilities, its focus on developer enablement, and its integrations with popular development tools.





